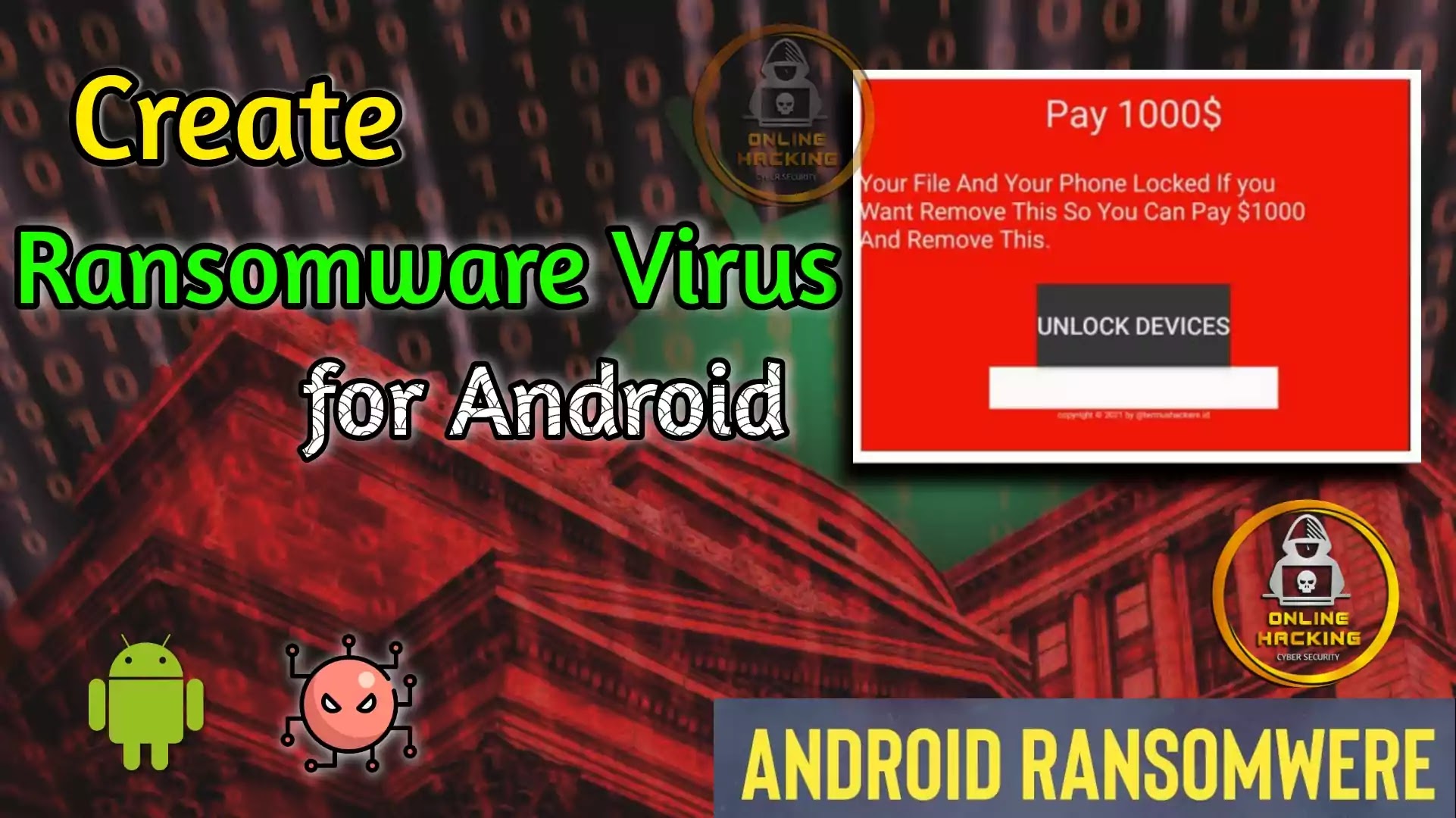
What is Ransomware?
Ransomware is a type of malicious software (malware) that often uses encryption to threaten the release of data or computer systems, or restrict access to data or computer systems until the victim has paid the ransom to the attacker. If the victim does not pay on time, the data will disappear permanently.
Today, ransomware attacks are commonplace. Large corporations in North America and Europe have become victims of this trend. Cyber criminals target any buyer or business, and the victims come from a variety of industries.
Many government agencies, including the FBI, advise against paying taxes to avoid starting a ransomware cycle, such as Project No More Ransomware. In addition, perhaps half of the ransomware victims may have experienced repeated ransomware attacks.
Categories of Android Ransomware
How Android Ransomware Malware Works
- Build Notifications: Once Android ransomware is installed on the device, it starts building a notification containing the ransom notification. It uses the setCategory function (“call”) to indicate that the notification is very important and requires special privileges.
- Hijacking the Screen: A notification is stored on the user interface (GUI), and when a user clicks on the notification with any pre-defined scans, the API pushes the ransomware notification window using the setFullScreenIntent () functionality.
- Blocking the users to access anything else: As soon as the ransom caption appears on the screen, it blocks the operation of onUserLeaveHint () on an Android device. That means, even if users tap the back button to turn off captions, they will be prevented from doing so. If they attempt to use any other phone functionality, the main screen will not show you, and the top screen will remain the same with the redemption notification.
REQUIREMENTS Dependencies :
- Java
- Openjdk 11
- Aapt
- Apktool
- Apktool 2.4.0
- Zipalign
- Imagemagick
- Python3
- Python3-pip
- Pillow
- Java
- Openjdk 11
- Aapt
- Apktool
- Apktool 2.4.0
- Zipalign
- Imagemagick
- Python3
- Python3-pip
- Pillow
Installation Android
Install Android :
Step 1:- Fast Run Free Cloud Linux Your Android Devices read this Post & Articles how to setup & run free cloud linux
Also Read : Cloud Linux RDP Desktop Lifetime Free for Google Cloud Console
Step 2:- Using Linux Installation Commands Step by Step
Installation Linux
Step 1:- Update and upgrade to Linux OS To avoid errors while installing Gpredict to steal sensitive information. If your Linux version does not automatically update the list of cache software after adding one, you will need to update it by typing:
Step 2 :- Install Repository Packages
Step 3 :- Now all the dependencies have been installed on your termux and we can now install the SARA Simple Android Ransomware tool on the Linux using the command given below. The file size of this tool is very simple, just copy and paste the command below and the tool will be loaded in 10 seconds.
Once you execute the above command it will ask app name, app icon (png), title, and description, unlock key. so you fill in the all required details.

Fix Error
Read this Post & Articles how to setup & run Free Cloud Linux
Also Read : Cloud Linux RDP Desktop Lifetime Free for Google Cloud Console



SOCIAL MEDIA